ClamAV Antivirus is an open source malware detection tool. In this tutorial we cover getting started with ClamAV and common use cases.
Through various configuration profiles it is able to perform real time filesystem detection, ad hoc file scanning, mail gateway filtering and http proxy scanning.
These use cases only scratch the surface of what is possible using the core engine and various open source addon components.
ClamAV and the key development team were acquired by SourceFire in 2007. Now maintained by Cisco Talos, after the acquisition of SourceFire in 2013. You may have heard of Cisco, a small startup that makes networking equipment.

Installing ClamAV on Ubuntu (or Debian)
To get the very latest version, or if a custom build is required installation from source would be necessary. However, using an Antivirus package in production is something that you want to be stable, secure and easily patched when security updates are released. For this reason I recommend using the Stable version of ClamAV from the Ubuntu repositories.
While the ClamAV core version will be not be the very latest release you will still be receiving the latest updates to the Antivirus signature database through the freshclam updates.
root@8ca32fd2f888:/# apt update
root@8ca32fd2f888:/# apt install clamav
root@8ca32fd2f888:/# clamscan --version
ClamAV 0.103.2
root@8ca32fd2f888:/# freshclam
It is as easy as that. I quickly spun up an Ubuntu 20.04 Docker image and ran the installation. The clamscan version is 0.103.2.
Running freshclam will ensure the latest database is available, updates to the signature database are made once or twice daily, so put freshclam in a cron job to keep things fresh.
root@8ca32fd2f888:/# clamscan /usr/bin
<< SNIP >>
/usr/bin/ucf: OK
/usr/bin/openssl: OK
/usr/bin/ucfq: OK
/usr/bin/crontab: OK
----------- SCAN SUMMARY -----------
Known viruses: 8528798
Engine version: 0.103.2
Scanned directories: 1
Scanned files: 287
Infected files: 0
Data scanned: 20.16 MB
Data read: 22.85 MB (ratio 0.88:1)
Time: 23.066 sec (0 m 23 s)
Start Date: 2021:05:13 00:04:35
End Date: 2021:05:13 00:04:58
A simple directory scan is performed by running clamscan against the folder name. If you need a quick antivirus solution, installing ClamAV, updating and starting the scan can be done in a few minutes.
ClamAV Signatures and Coverage
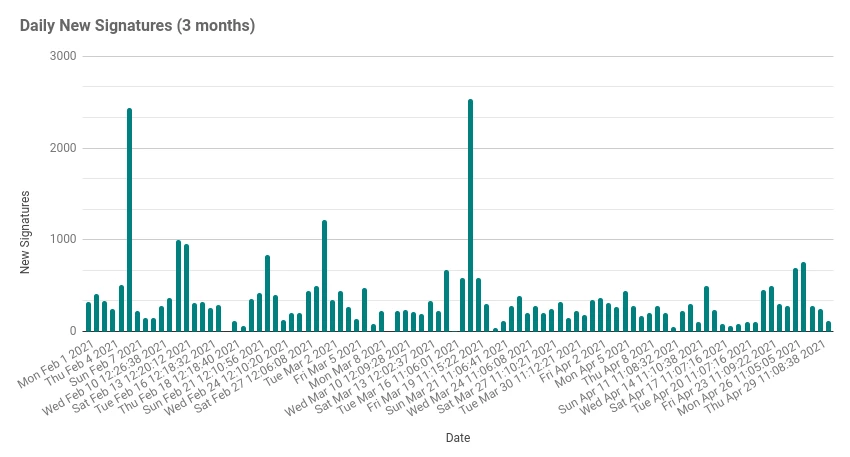
At the time of testing the latest signature count is 8528798. Updates are regularly released with the following chart showing the number of new antivirus signatures daily over the 3 months to April 2021.
Testing ClamAV against a PDF with an embedded DOC
Didier Stevens created a handy test file that contains the well known EICAR test file, however the file is dropped from a DOC that is embedded within a PDF.
https://blog.didierstevens.com/2015/08/28/test-file-pdf-with-embedded-doc-dropping-eicar/
By design accessing this file (after unzipping with password) should cause your Workstation AV to light up and will potentially send alerts to your IT department.
root@8ca32fd2f888:/# clamscan pdf-doc-vba-eicar-dropper.pdf
/pdf-doc-vba-eicar-dropper.pdf: Doc.Dropper.Agent-1540415 FOUND
----------- SCAN SUMMARY -----------
Known viruses: 8528798
Engine version: 0.103.2
Scanned directories: 0
Scanned files: 1
Infected files: 1
Data scanned: 0.06 MB
Data read: 0.01 MB (ratio 7.50:1)
Time: 17.054 sec (0 m 17 s)
Start Date: 2021:05:13 00:14:55
End Date: 2021:05:13 00:15:12
root@8ca32fd2f888:/#
Understanding clamd, clamdscan and clamscan
When you run clamscan the libclamav engine and signatures are loaded at runtime. The other way to run the scanning engine is via clamd.
Clamd runs as a background process that has the engine and signatures in memory. A clamd client (clamdscan) then connects to the service in order to have the scanning performed. The clamd service accepts various commands in order to perform the scanning.
Configuration of the scanning is controlled via the clamd.conf configuration and cannot be specified at runtime. Whereas using clamscan it is possible to configure a large number of options at runtime from the command line.
Note that the clamd service is unauthenticated. Do not make it accessible from the Internet.
Integrate ClamAV in a HTTP Proxy
By integrating ClamAV into a HTTP proxy such as Squid it is possible to have transparent antivirus across all your web traffic.
Using Squid it is possible to configure the proxy to perform SSL/TLS bumping (decryption) enabling scanning of SSL/TLS encrypted traffic.
squidclamav icap module
Squid is a popular open source HTTP proxy that can work with modules using the ICAP protocol. ICAP is standard that allows HTTP proxies to outsource content inspection and manipulation to an external process or server.
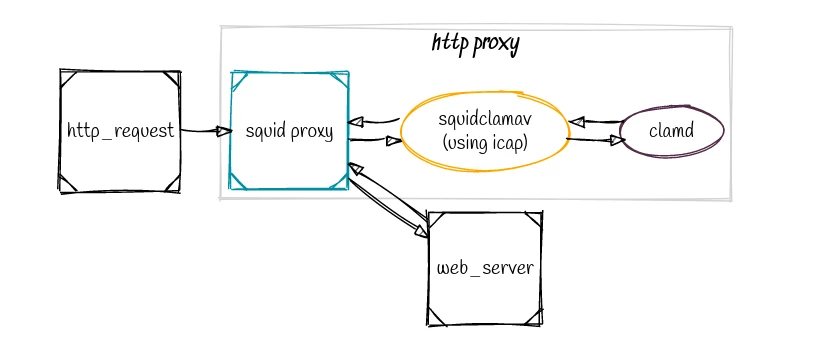
SquidClamAV is an antivirus for the Squid proxy based on ICAP, it is highly performant and able to handle thousands of HTTP connections simultaneously.
Installation and Configuration of SquidClamAV goes beyond the scope of this guide.
Conclusion
Even if you already have a commercial antivirus solution within your environment, knowing that you can quickly spin up ClamAV in a few minutes to perform ad hoc testing is definitely something to keep in your grab bag of tools.
Like Vulnerability Scanning, using multiple solutions and signature databases will ensure you get the best coverage in detecting and understanding the threats to your environment.
Running ClamAV on gateway servers (SMTP / HTTP) is a popular solution for companies that lean into the open source world. With a team run out of Cisco Talos, it is no wonder that this software continues to kick goals for organisations of all sizes.
Next Level Your Technical Network Intelligence
- 13 Vulnerability Scanners
- 17 Free DNS & Network Tools
- 4+ Billion Records of DNS / IP data
